Explain Different Kinds of Online Threats in Hindi
Sign up Save Calculate the price of your order. The website has an average trust rating and no active threats have been reported by users recently.

Online Education Not A Threat But A Boon For Higher Education Indiabioscience
Encircle your answers on the separate answer sheet.

. We accept only Visa MasterCard American Express and Discover for online orders. Your personal details remain confidential and wont be disclosed to the writer or other parties. In the film Rai also included a short narration on the meaning of.
Later on this practice was discontinued and in as much as I remember since past 15-16 years. Then finish CodeHS Unit 8 or move on as 2. 1 Assessment opportunities 27 4.
He may be given appropriate security by the concerned state police when he travels out. New to Essays Assignment. Extensive validity scales to detect and corr ect for these kinds of biases.
Google Ads Search Certification Exam Answer 2020 Updated. For example if the Chhattisgarh CM is assessed to have a threat from Maoists only in his state the Centre may chose to give him residence and mobile security only in his state. Desai was asked to explain the same by the DG on 04102019 to which he stated I would like to explain that it was a practice at NECC that subsidy was given to traders for keeping eggs in cold stores so that the NECC price of eggs is maintained in the market.
For the rest however the way these kinds of films are going is pretty trivial. E NEO inventories do not. The d and f block Elements.
Type of paper needed. They should take on a different role in their team than they did in the last activity. 6241-265-1pass-006-r04indd 239 6241-265-1pass-006-r04indd 239 12242013 41212 AM 1224.
Different VIPs are given different kinds of security cover depending upon the threat perception. The interim pathway for caregivers is a limited time pathway to. You will get a personal manager and a discount.

Cyber Threat Basics Types Of Threats Intelligence Best Practices Secureworks

10 Types Of Identity Theft You Should Know About Info Savvy Identity Theft Identity Competitive Intelligence

How To Remove Malware On Your Windows Pc Hp Tech Takes

15 Alarming Cyber Security Facts And Stats Cybint
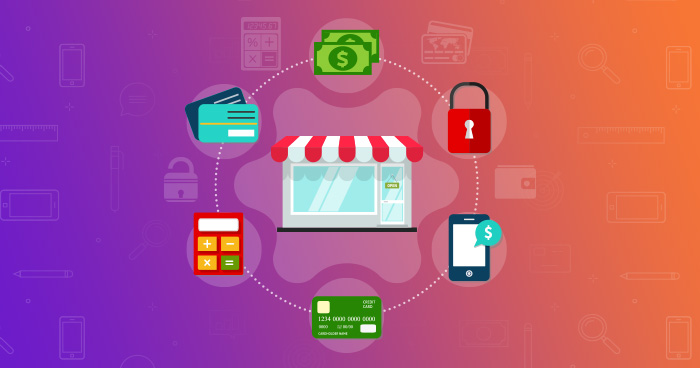
13 Top Ecommerce Security Threats And Solutions Of 2022

What Is A Network Security Key A Crucial Digital Security Concept

Types Of Cyber Attack Or Threats

Explain Different Types Of Online Threats Brainly In

What Is A Network Security Key A Crucial Digital Security Concept
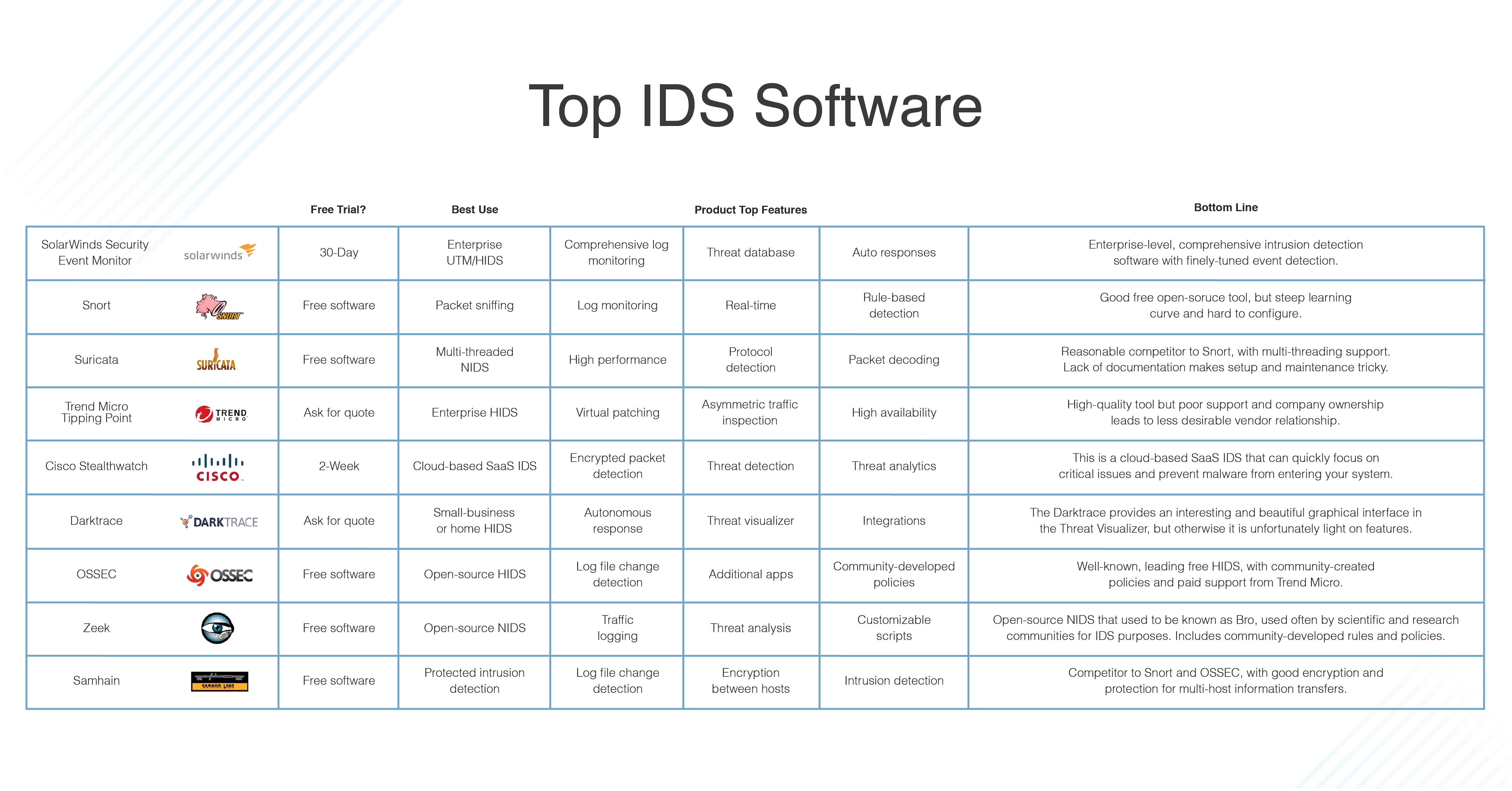
What Is An Intrusion Detection System Definition Types And Tools Dnsstuff

Concept Of Safety Culture And Its Assessment Indicators Safety Management System Workplace Safety Safety Slogans
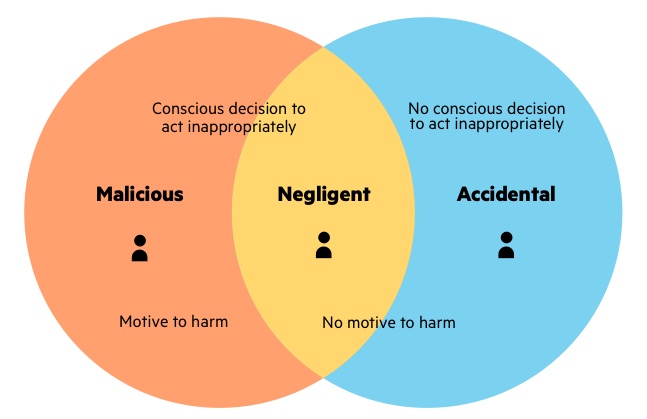
What Is An Insider Threat Malicious Insider Attack Examples Imperva
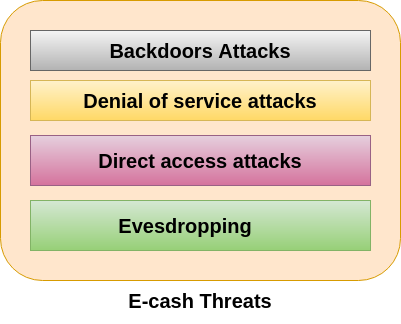
Security Threats To E Commerce Javatpoint

Cyber Crime Types Examples And What Your Business Can Do

What Is A Network Security Key A Crucial Digital Security Concept

What Are The Different Types Of Computer Viruses Uniserve It

How To Create Google Form Step By Step In Urdu Hindi 2018 Google Forms Online Surveys Online Tests

What Is The Difference Between A Threat A Vulnerability And A Risk Sectigo Official

Comments
Post a Comment